BBC Bug Bounty Write-up | XSS Vulnerability
This is a write-up about the XSS Vulnerability which I found on the BBC website.
I came across BBC’s Bug Bounty program and decided to give a try.
I picked http://www.worldservicepartners.bbc.co.uk/ as my target (domain unavailable, as BBC terminated the domain recently).
On visiting the domain, there was a login page but there’s no registration / signup feature to utilize the login form.
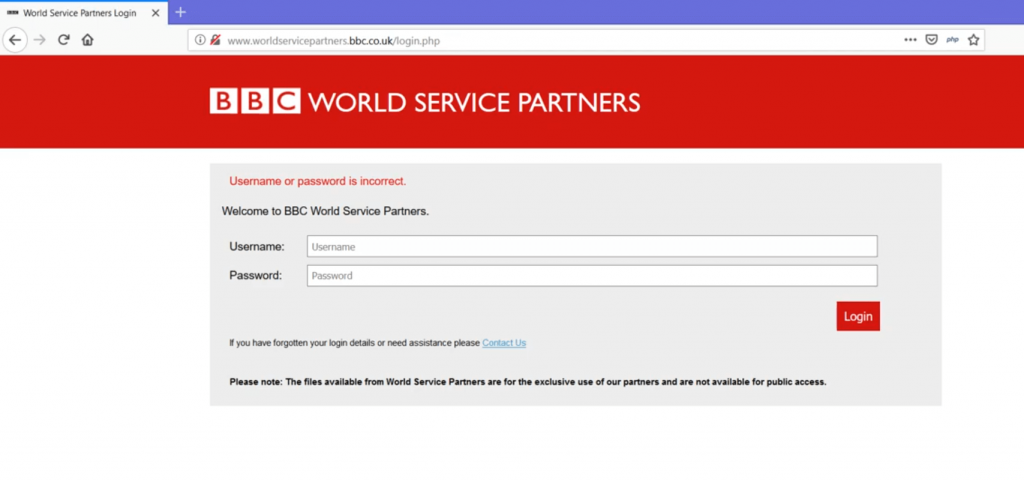
As there were no other input fields other than the login panel itself, I used some tools to find the parameters, but no luck. I couldn’t find any input parameters.
So I decided to play around with login form and tried SQLi and other input related vulnerabilities.
On firing up the burp and intercepting the login request, I found a couple of hidden parameters alongside the username and password input field.
username=123&password=456&dest=xgysk&iframe=
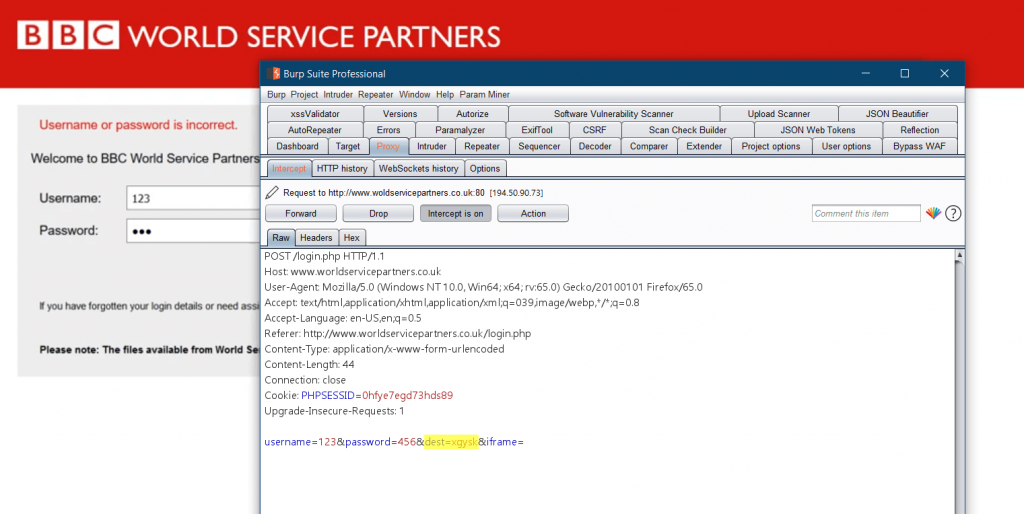
Notice the hidden parameter dest and iframe in the request. I tried possible attack vectors for SQLi, XSS and other input validation vulnerabilities.
I noted that the traditional XSS payloads such as didn’t trigger an XSS. So I used Javascript Event Handlers which perform an action based on certain events such as onmouseover, onmouseclick, etc.
NOTE: Using of event handlers requires user interaction such as mouse click or key press.
I understood that the browser is ignoring the javascript events such as onclick and onmouseover. So the execution of XSS is limited to access keys using the following payload.
“accesskey=”x”onclick=”alert(document.domain)”//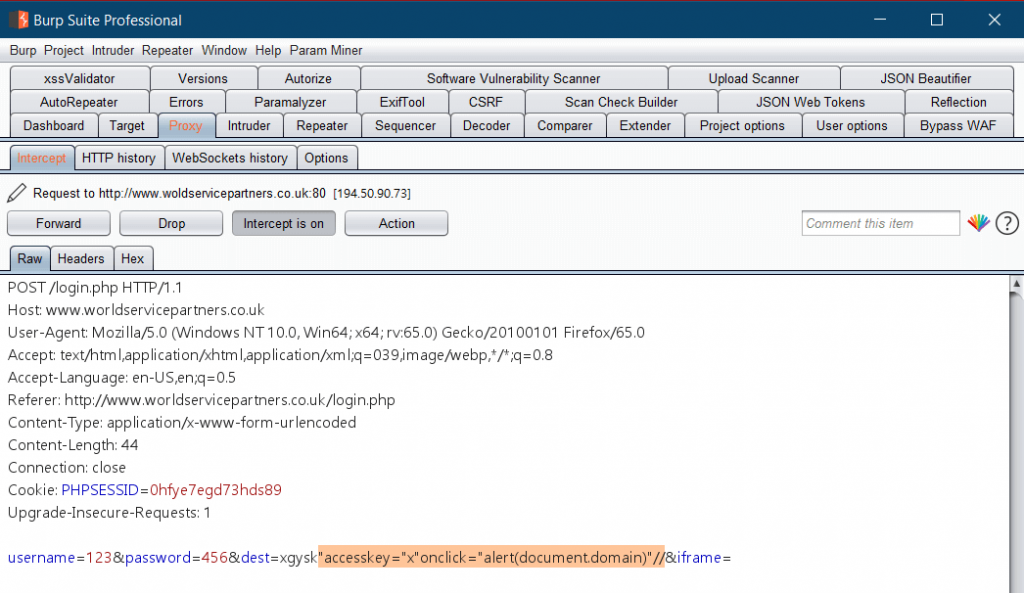
Notice the parameter dest= containing the specially crafted XSS payload.
When the request is made, the page loads normally. To trigger an XSS, we will need to use the following key combinations to get the Alert box.
(Press ALT+SHIFT+X on Windows) or (CTRL+ALT+X on OS X)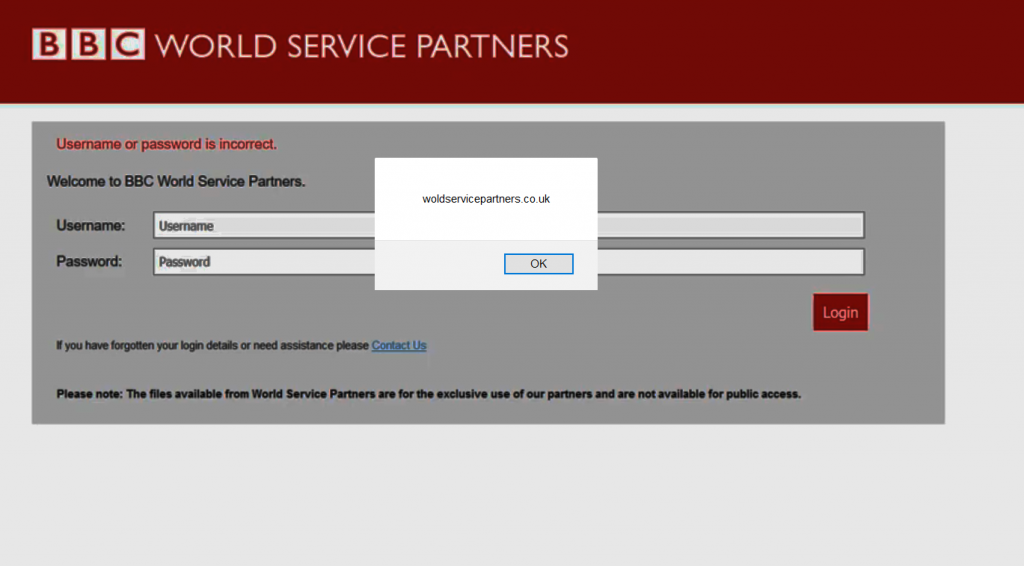
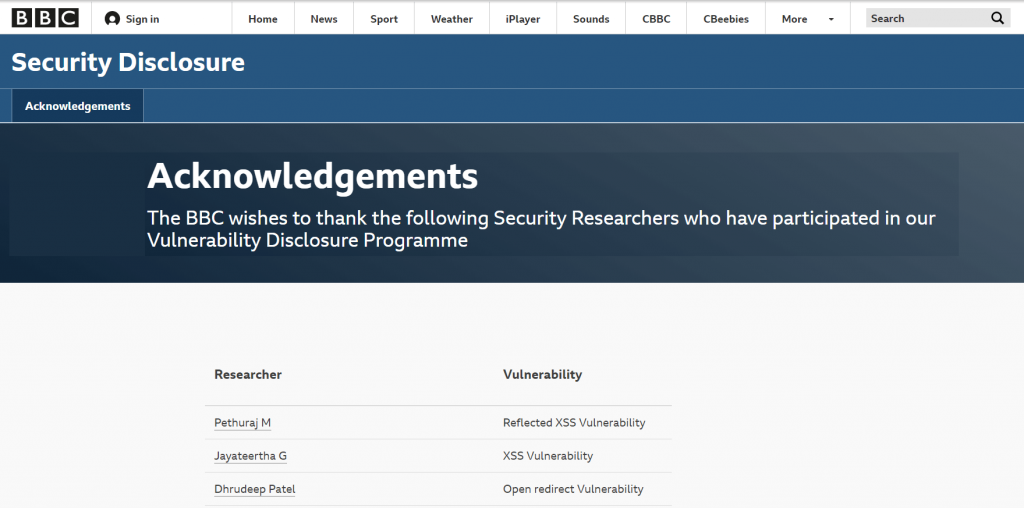
After reporting this issue to the BBC Security Team, I’m honored on their Hall of Fame page and presented with a BBC T-Shirt.
Here’s the cool T-shirt from BBC 👕

Thanks for reading this article. Hope you liked it.
To find all my Acknowledgements / Hall of Fames / Bug Bounty journey, Visit https://www.pethuraj.in
Stay tuned for more writeups.
Get in touch with me –
https://twitter.com/Pethuraj
https://www.linkedin.com/in/pethu/
You may like

How to use Burp Suite Like a PRO? PART – 2



