Cyfe.com – CSRF Vulnerability Writeup
Hi infosec folks, Here is a writeup on how I am able to do a CSRF attack on one of the subdomains of Cyfe.com.
This bug could allow an attacker to force a user in cyfe.com, to make certain requests which would allow modifying the user account details. This is possible because the website www.cyfe.com doesn’t implement any security measurements like special tokens or headers to prevent CSRF attacks.
So as usual I started with recon and decided my target subdomain. After trying for different attack vectors I noticed that there is no CSRF tokens in the Http Request. So as obvious I decided to go for a CSRF attack. I explored the application and able to find an update profile page where there is an endpoint for email preferences.
For CSRF attack we would require two accounts, one for attacker other for the victim. I signed up on both the accounts and went to update profile and uncheck the email preferences from attacker’s account. By default on both the accounts, the email preference field is checked.
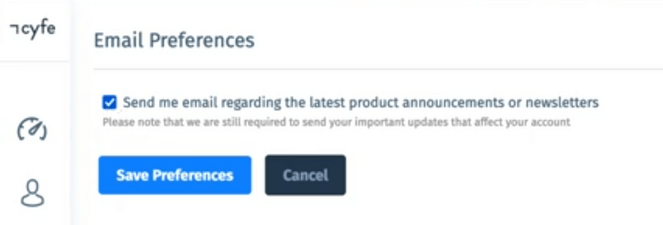
I intercepted the request and generated CSRF POC.
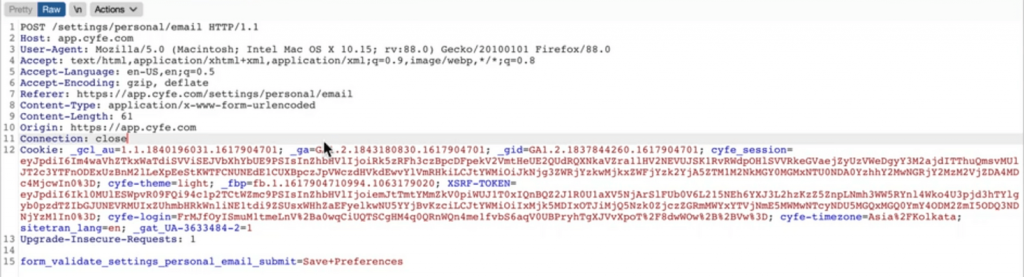
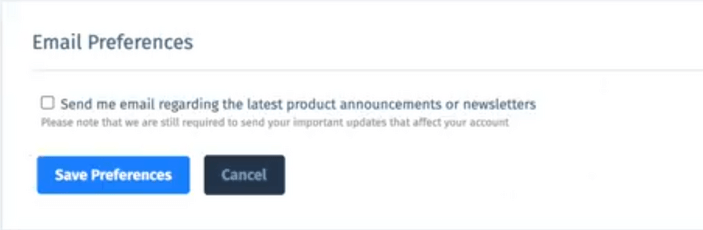
The generated CSRF POC is a html file with hidden parameters and submit button to check the email preferences field. Send this html file to victim or opened it in the victim’s browser. The victim will click the submit button and boom it will lead to uncheck the email preference field in victim’s account that’s a forged request.
Glad to secure Cyfe asset from CSRF attack. I hope you like this writeup and below is the Hall of Fame from the Cyfe Team.
Get in touch with me –
https://twitter.com/Pethuraj
https://www.linkedin.com/in/pethu/
You may like!

How to use Burp Suite Like a PRO? PART – 2