Houzz – SSRF Vulnerability Bugbounty Writeup
Hello Infosec folks, here is a new and interesting writeup for you all. It’s about how I found Server Side Request Forgery vulnerability on the Houzz domain. Let get started.
Server-side request forgery (also known as SSRF) is a web security vulnerability that
allows an attacker to induce the server-side application to make HTTP requests to
an arbitrary domain of the attacker’s choosing.
In a typical SSRF attack, the attacker might cause the server to make a connection to internal-only services within the organisation’s infrastructure. In other cases, they may be able to force the server to connect to arbitrary external systems, potentially
leaking sensitive data such as authorization credentials.
Lets get started with houzz application. I have signed up and logged into the main
domain URL. I explored the site and its various functionalities and then my eyes caught an endpoint to upload an image via web so I thought of playing with such an interesting functionality. Tried different attack vectors on this endpoint but there was no luck.
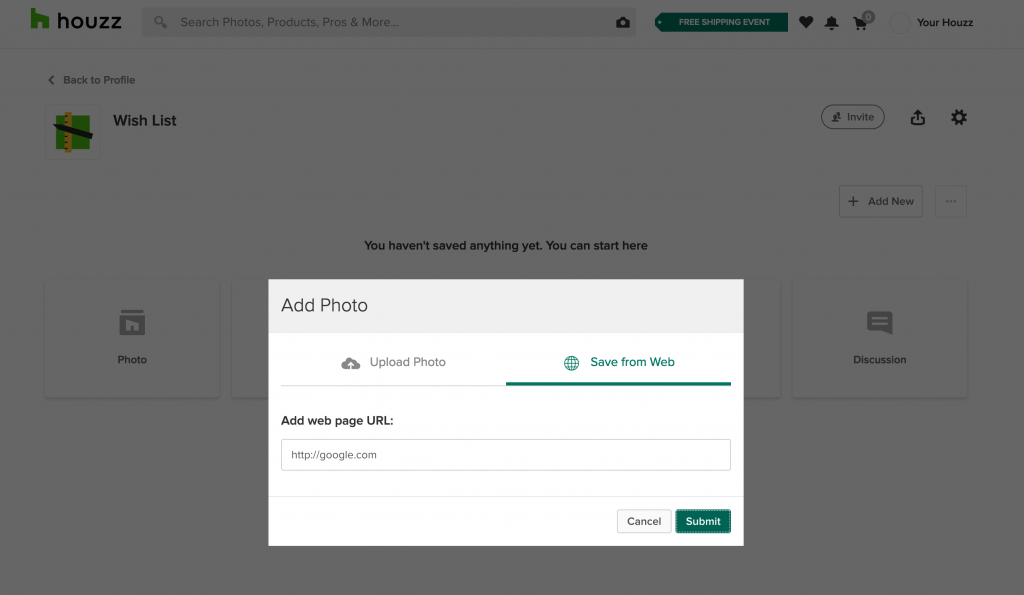
After all the failed attempts of different payloads for different attacks. I tried with any
random URL in “Add web page URL” text field, captured the Http request on Burp Suite and
sent it to the repeater for further inspection.
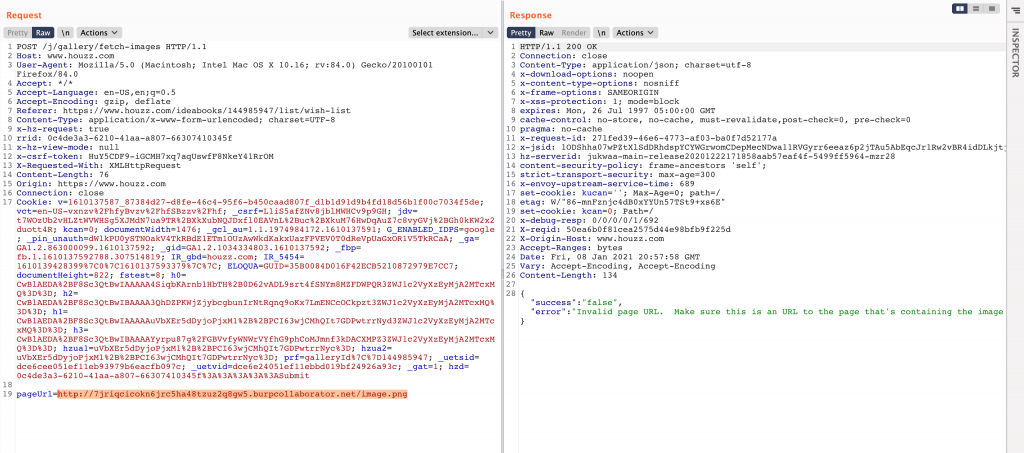
As shown in the Http request in the above snapshot, I quickly sent this to Burp Collaborator
and replace the random URL with Collaborator URL and hit send, observed the
following Burp Collaborator request as shown which is hitting HTTP and DNS
requests on Burp Collaborator Client.
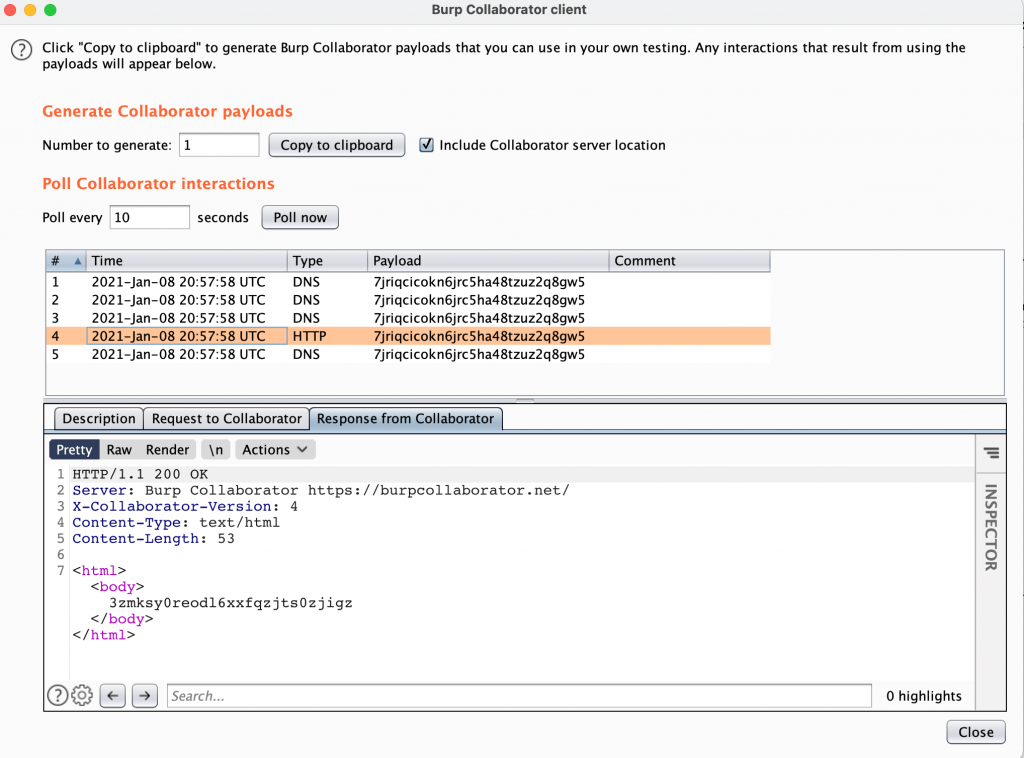
Finally, a successful SSRF attack!! I could have exploited this attack to perform internal port scan, to escalate to command injection and to infiltrate the data. But I stopped with this and reported to their security team. Hope you liked the writeup.
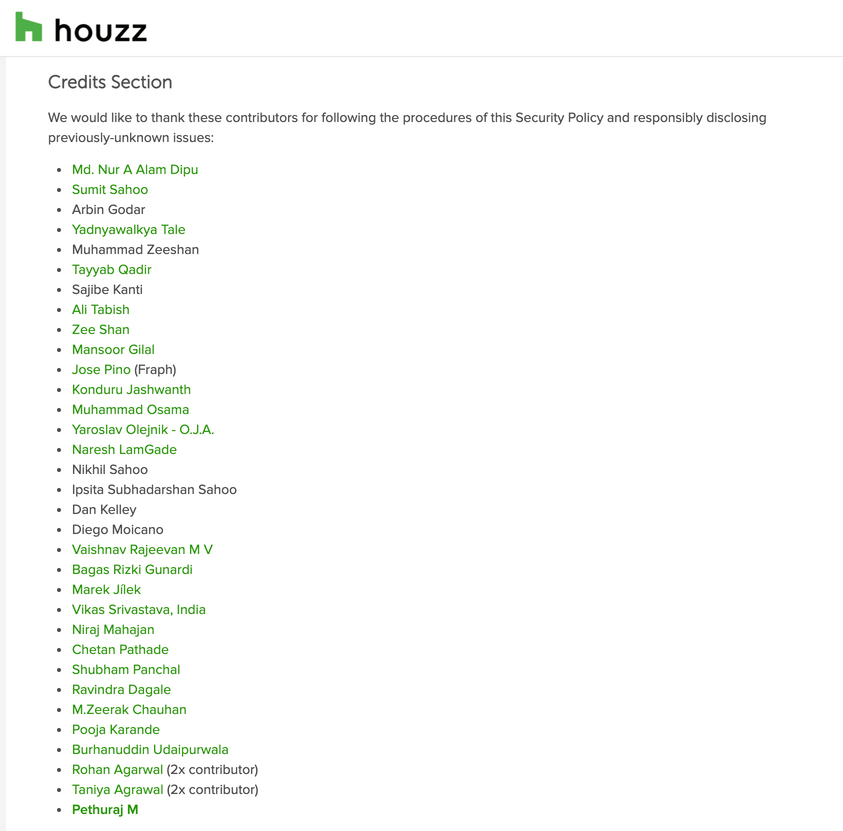
For reporting this vulnerability to the Houzz Security Team responsible, I’ve been acknowledged in their Hall of Fame page – https://help.houzz.com/s/article/Houzz-Security-Policy?language=en_US
Stay tuned with my blogs to get more exciting writeup. Happy Learning and Happy Hacking!!
Get in touch with me –
https://twitter.com/Pethuraj
https://www.linkedin.com/in/pethu/
You may like!

How to use Burp Suite Like a PRO? PART – 2

