United Nations IDOR Vulnerability Writeup
Here’s the writeup on the IDOR Vulnerability that I found on the United Nations web portal.
I selected my target as United Nations and started with recon and enumerated all the subdomains.
After selecting the target as ideas.unite.un.org, I was able to find the registration and login pages and tried exploring different attack vectors.
I quickly signed up with two different accounts and performed testing on different endpoints.
I observed that these accounts were passing respective unique account id which was easily guessable, while making any changes to the account.

So I decided to swap the account userId with the other account id and sent the request. I could able to perform successful IDOR vulnerability .
By taking an advantage of this vulnerability, I tried to change the language of the other user and it worked for me.

On intercepting the request for modifying the account details endpoint, the userId on the POST data can be tampered with other user id.
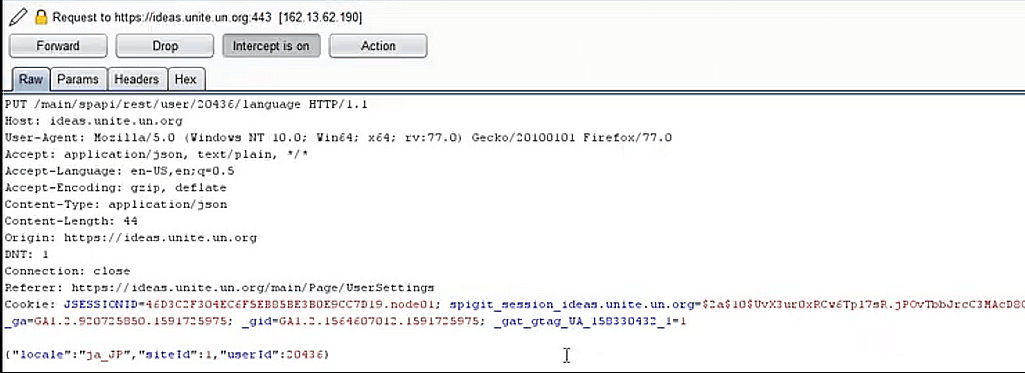
So with this, I’m able to successfully perform IDOR attacks and able to modify any other user account details. In this scenario, I changed the language of the other user.
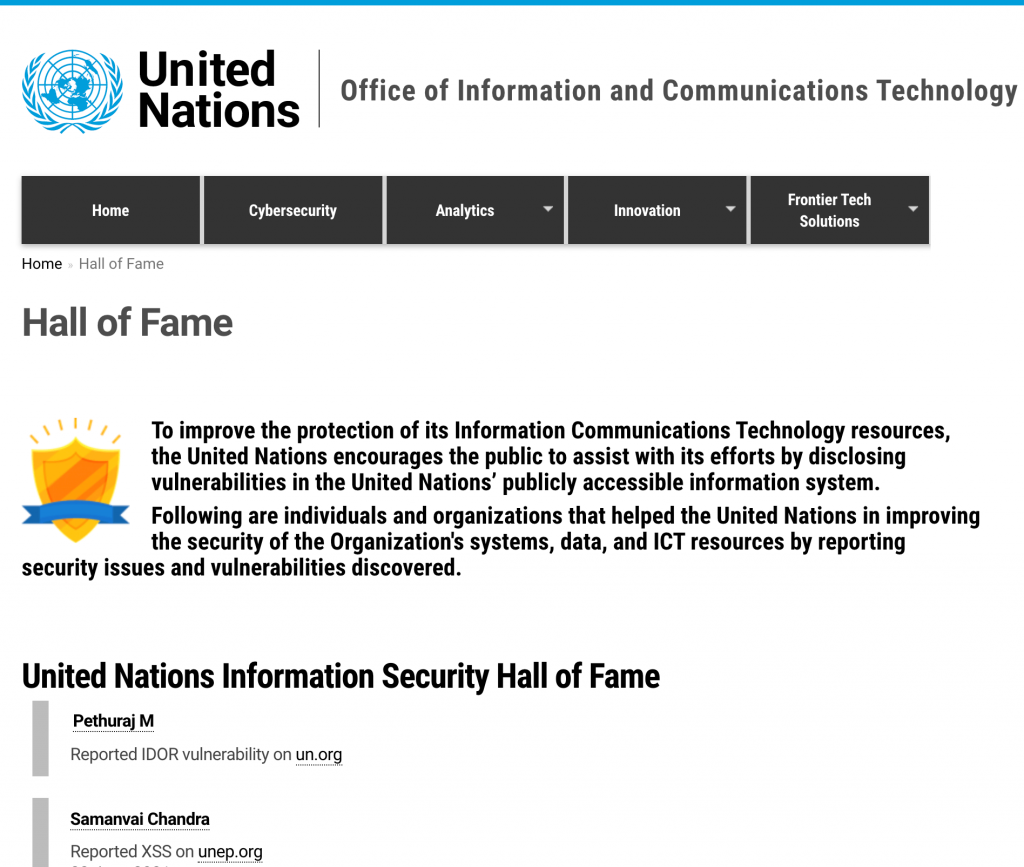
On reporting this issue to the United Nations Security Team, I was acknowledged on their Hall of Fame page for the second time ?
Get in touch with me –
https://twitter.com/Pethuraj
https://www.linkedin.com/in/pethu/
