Edmodo Bug Bounty Writeup
I found XSS vulnerability on one of Edmodo asset and it was found to be duplicate.
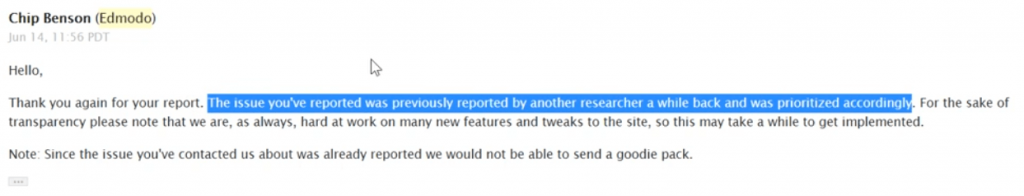
After my report got duplicated, I decided to bypass the XSS fix and started on the same target https://snapshot.edmodo.com.
The page looked like this and it has some input fields just like a form creation website.
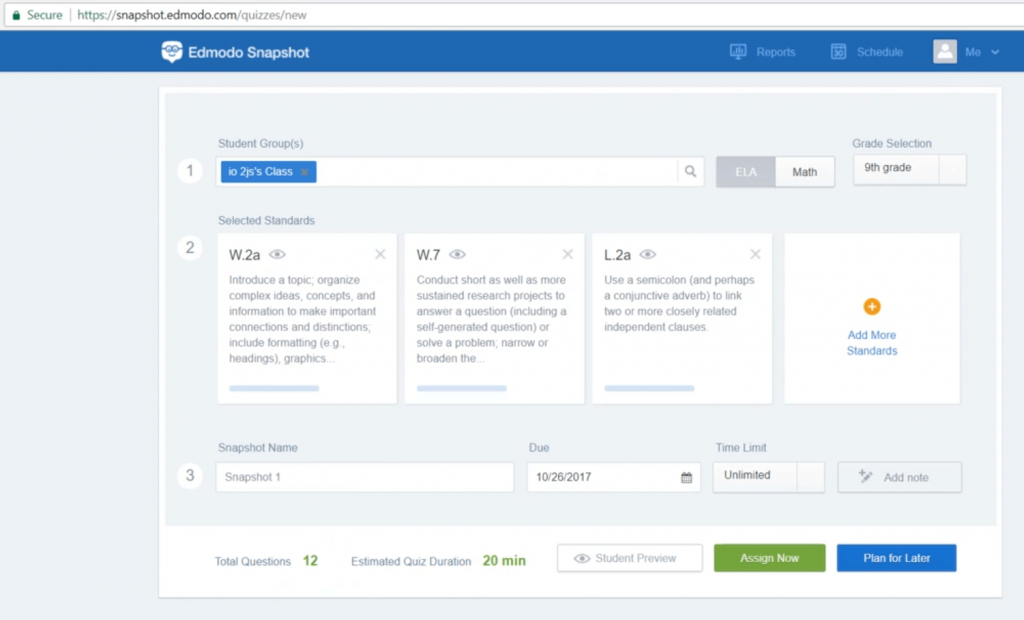
I tried the same payload which I reported earlier just to check if it’s fixed. And it is!
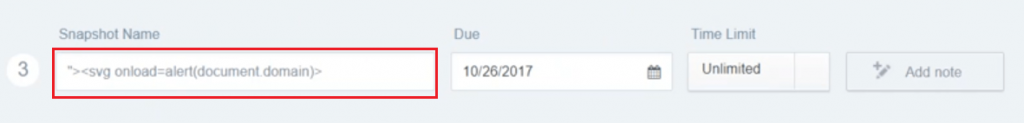
There is no popup and also I noticed the basic XSS payloads are being stripped off.
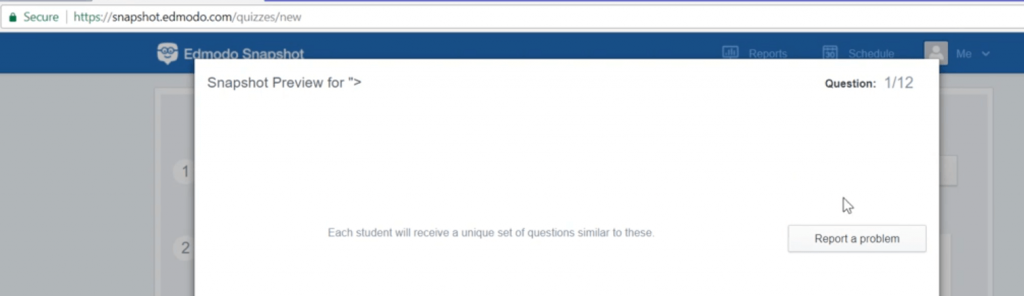
As you can see above screenshot, the payload didn’t execute. So I tried to understand the fix and decided to use encoded XSS payloads.
This time I used a base64 payload inside <embed> tag and it is a XSS.
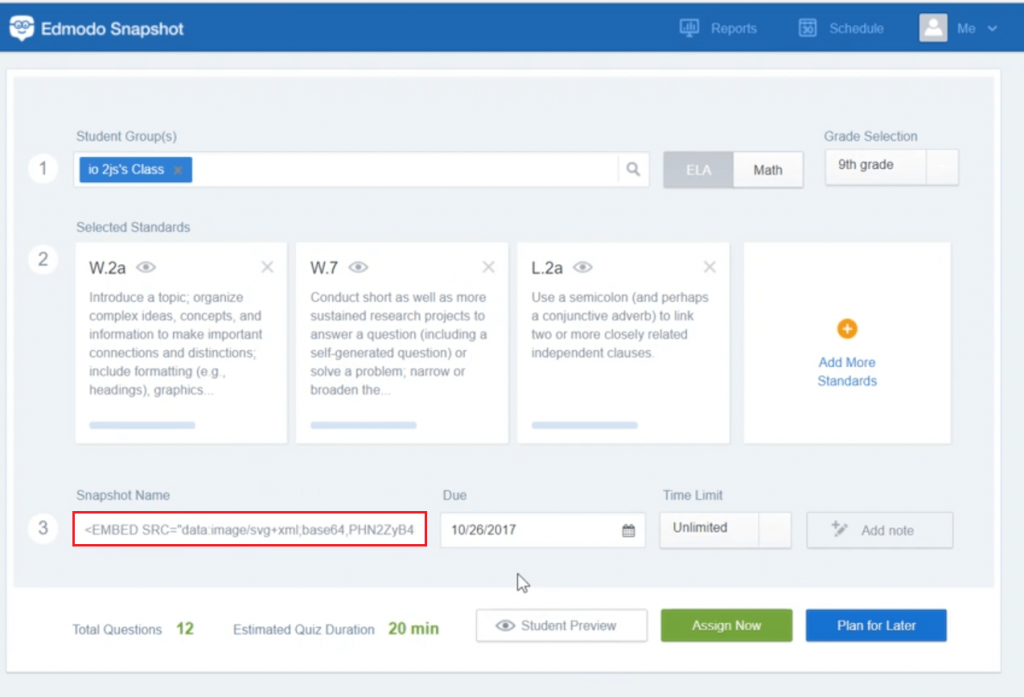
The payload executed and popped an XSS.
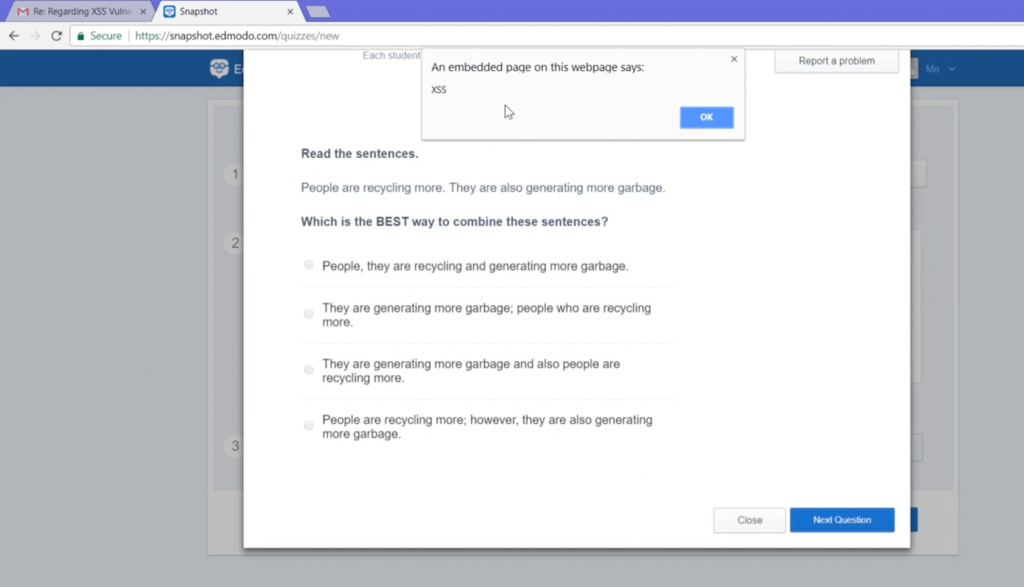
This payload is limited only to Firefox browser as by OWASP.

For reporting this vulnerability, Edmodo rewarded me for this vulnerability with exciting goodies.
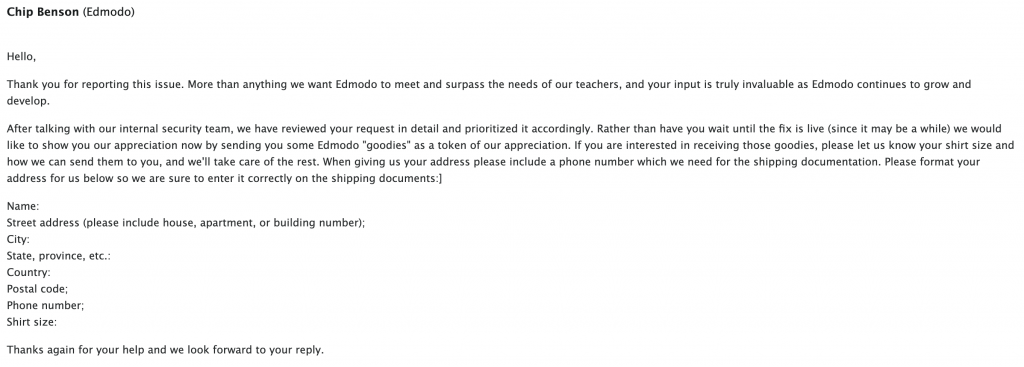
And after few days I received the swag pack!

Get in touch with me –
https://twitter.com/Pethuraj
https://www.linkedin.com/in/pethu/

How to use Burp Suite Like a PRO? PART – 2



