How I made to Paypal Bug Bounty $750
Hey Guys,
This blog is all about how I made to PayPal Bounty $750 with simple bug as Open Redirect Vulnerability. After deciding my target as PayPal, I read their responsibility disclosure program carefully and went through its scope.
Xoom was acquired by the PayPal and was in scope so I thought to make my hands dirty with Xoom domains.
The very first and obvious step I did was recon. I gathered all the valuable information and subdomains of the target Xoom. This vulnerability was found on Xoom Dashboard. Before proceeding to POC lets just understand about Open Redirect vulnerability.
Open Redirect Vulnerability
Open redirection vulnerabilities arise when an application incorporates user-controllable data into the target of a redirection in an unsafe way. An attacker can construct a URL within the application that causes a redirection to an arbitrary external domain. This behaviour can be leveraged to facilitate phishing attacks against users of the application, perform XSS attacks and also stealing tokens.
Vulnerable URL: https://refer.xoom.com
Vulnerable Parameter: redirect
The most strange part of this vulnerability is wherever I use redirect= parameter in the target domain, the website redirects.
Steps to Reproduce the vulnerability
- I opened up refer.xoom.com and navigated to pages which contains sensitive details in parameters as I can be able to perform open redirect and as well as token stealing.
- I randomly appended the URL with ‘&redirect=https://www.pethuraj.in’ which leads to redirection to the target domain. And I tried this in all the pages of Xoom dashboard and it worked.
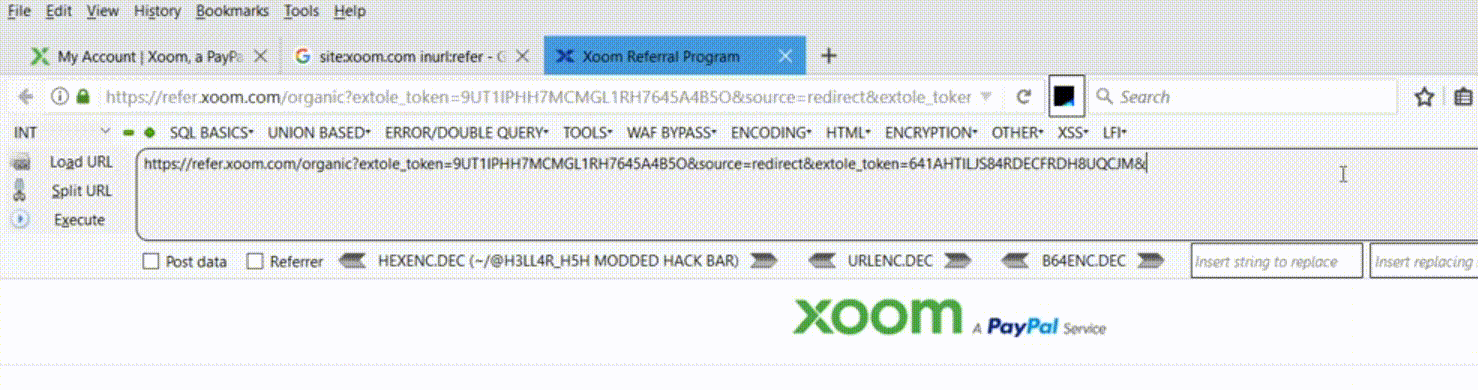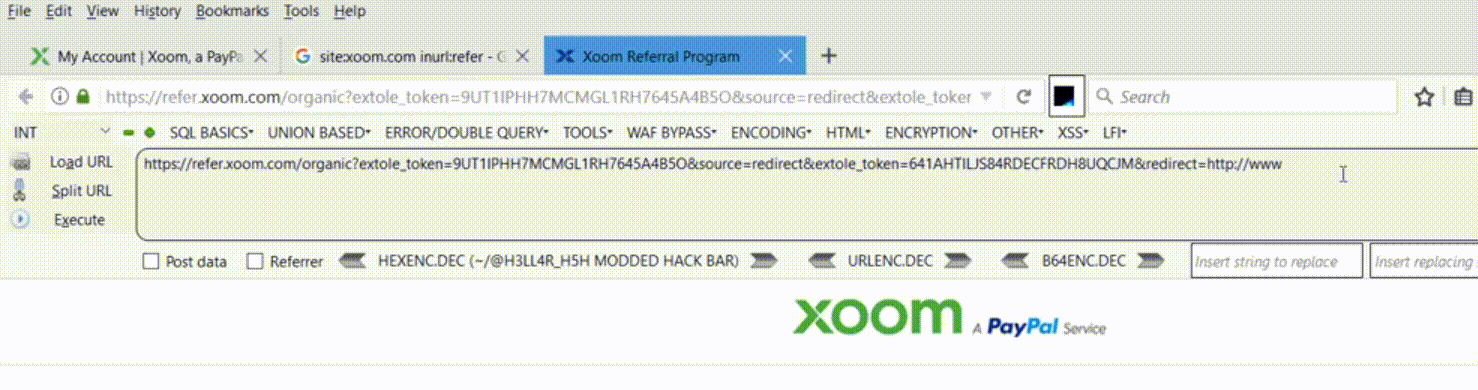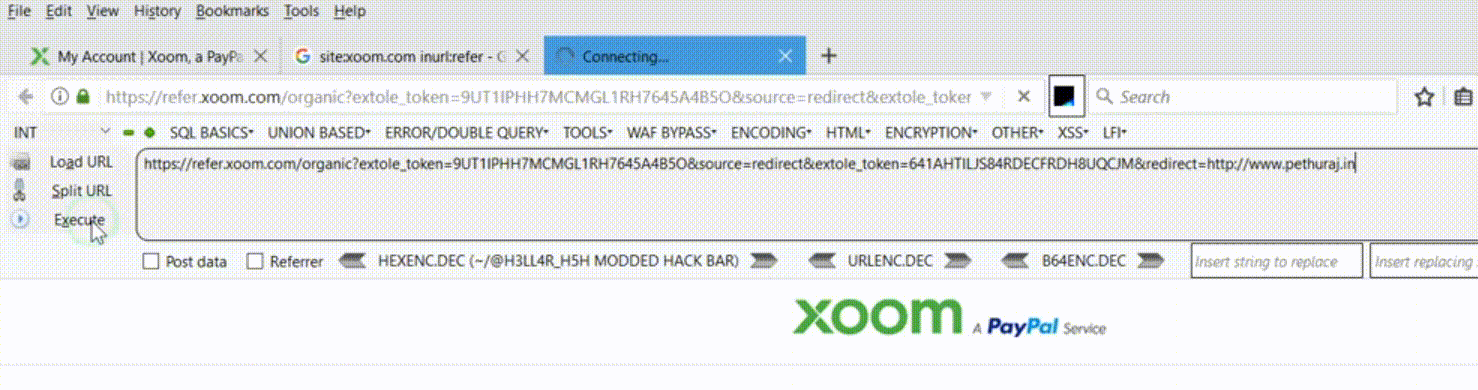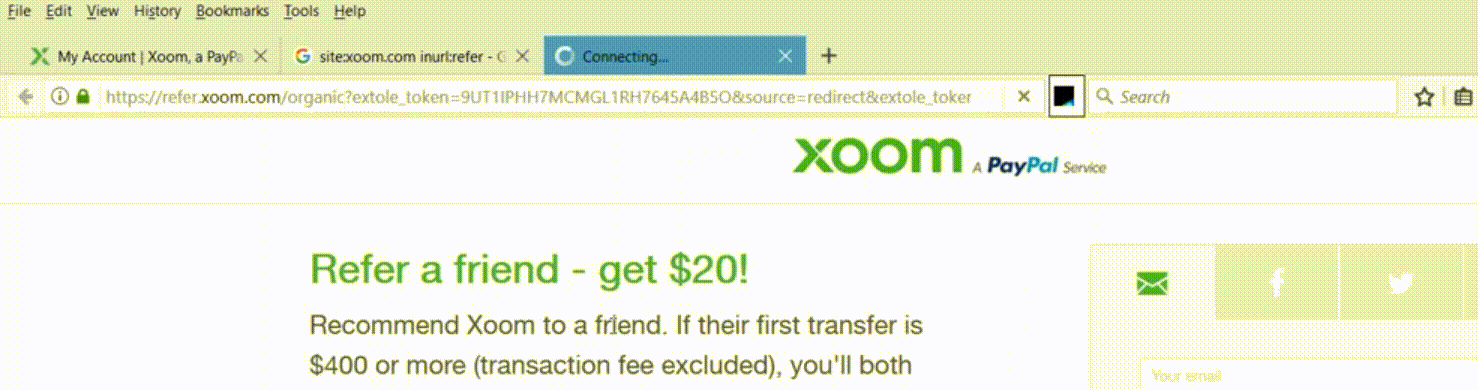
In simpler words, wherever the application is having redirect= parameter in the GET method – the redirect occurs.
Apart from Open Redirect, I was able to steal the tokens (campaign id) of the target website.
And regarding the token stealing, I set up a php code on my website which automatically logs all the incoming requests and then filter the campaign id separately.
I had reported the bug to Paypal immediately. Thanks to the Paypal team that they acknowledged the bug and rewarded me with bounty and acknowledgement on their Wall of Fame page.
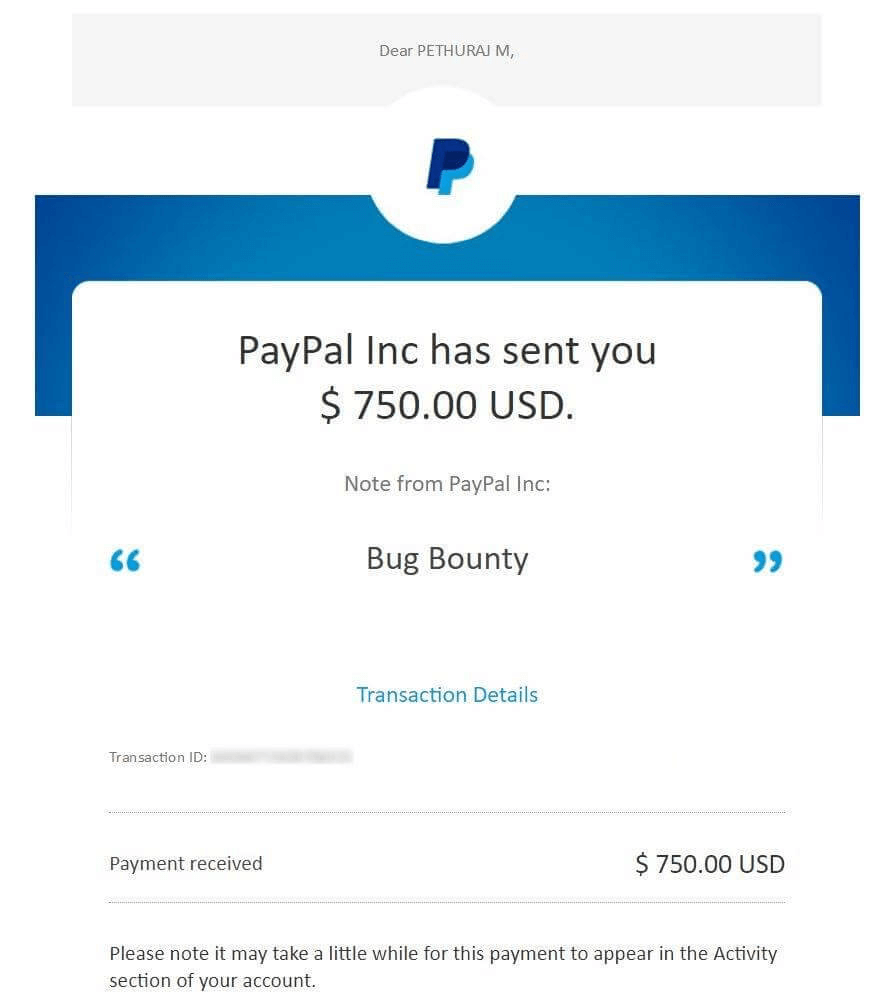
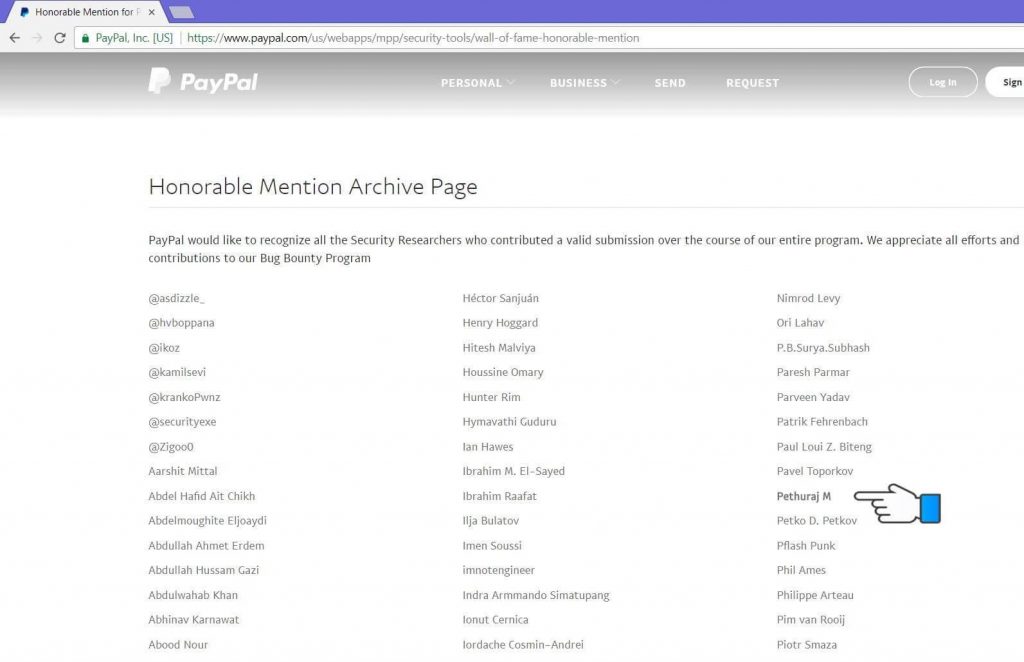
I hope aforementioned blog about open redirect vulnerability is easier to understand and hope there would be more blog coming on the way. Hope you like it.
Get in touch with me –
https://twitter.com/Pethuraj
https://www.linkedin.com/in/pethu/
You may like!

How to use Burp Suite Like a PRO? PART – 2