Bigbasket Bug Bounty Writeup
This is the writeup about the Bigbasket Open redirect bypass vulnerability.
I tested Bigbasket portal for security loopholes and I picked the main domain as the target.
I fuzzed the domain with tools like wfuzz, ffuf, dirb and using Burp’s Content discovery.
While the fuzz was in progress, I noticed the next= parameter containing a URL, which means I can try Open Redirect / XSS / SSRF issues on this parameter.
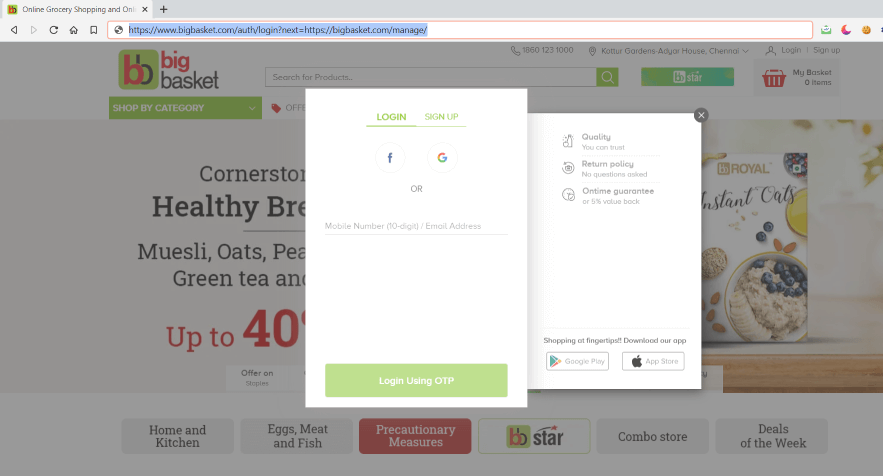
I tried open redirection by replacing my domain.
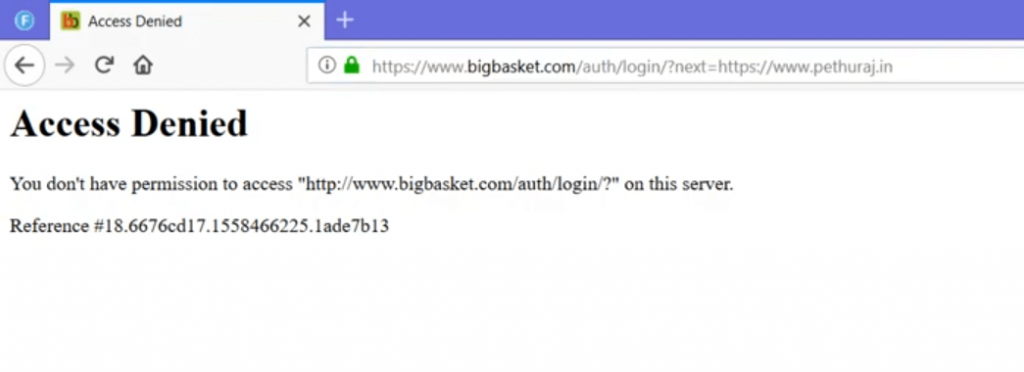
I got Access Denied error which means there is a validation for the domain in the next= parameter.
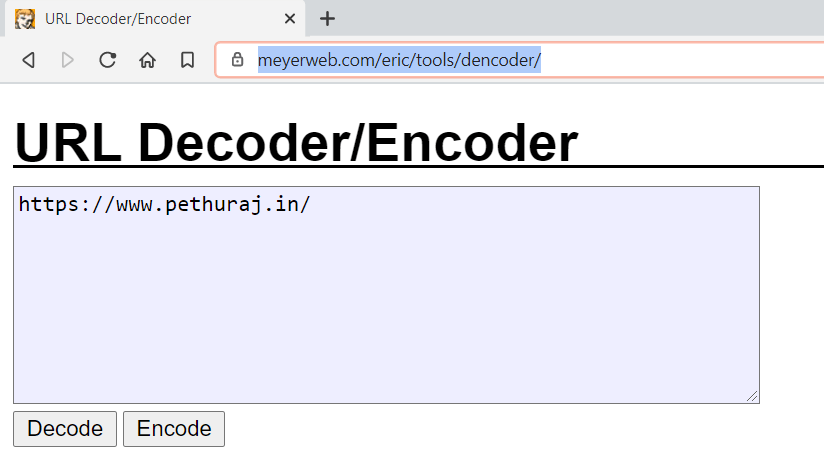
So as next step I encoded my domain using online HTML encoder.
I URL encoded my domain using this Online tool.
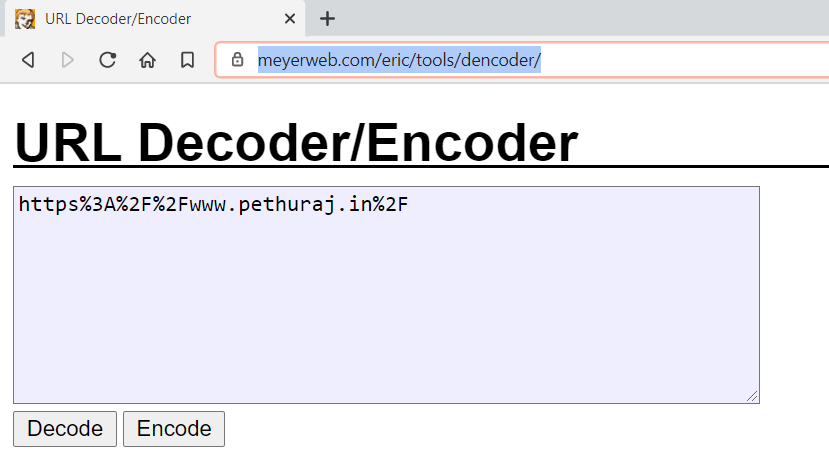
Now I used the URL encoded payload and inserted it on the next= parameter.
After I enter the credentials, and click Login – it redirects to my domain which is a successful Open redirect vulnerability 🎉
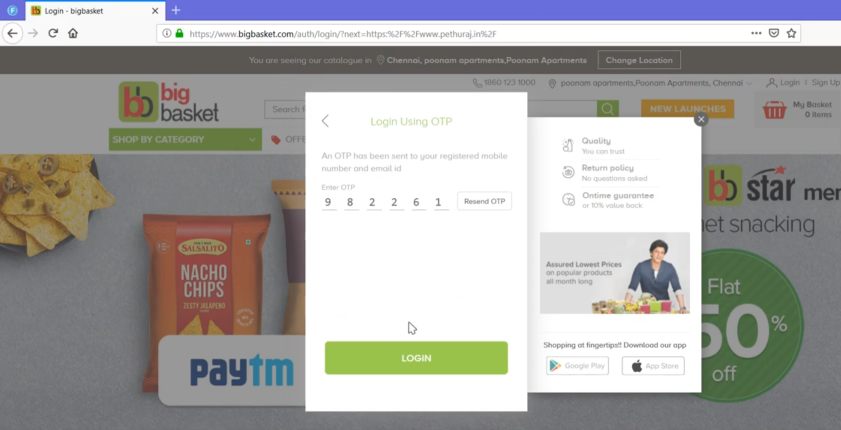
Below is the POC video.
POC Video :
💰 I’ve been rewarded by their Security team and acknowledged in their Hall of Fame.

Here’s the Hall of Fame.
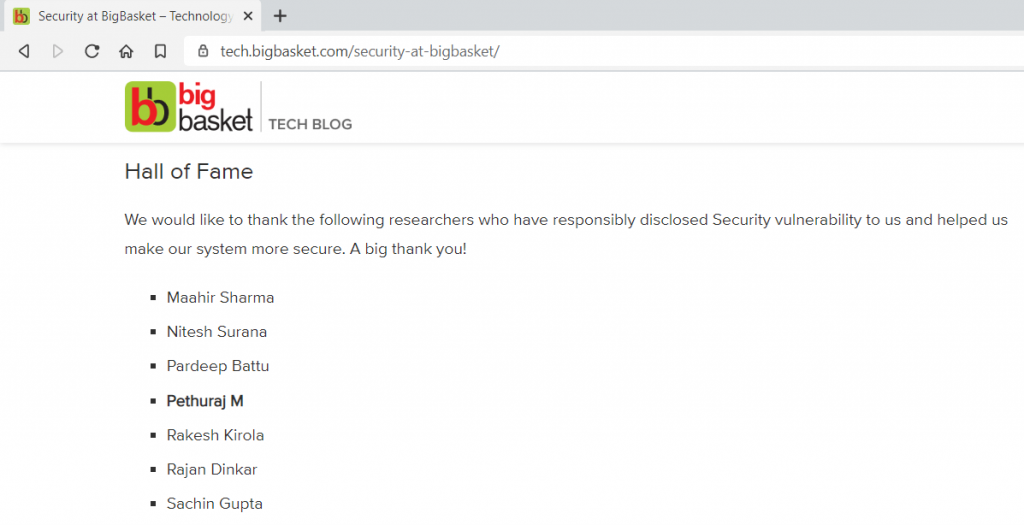
Bigbasket Hall of Fame – https://tech.bigbasket.com/security-at-bigbasket/
That’s it in this write up.
Thank you!
You may like

How to use Burp Suite Like a PRO? PART – 2