$3133.7 Google Bug Bounty Writeup- XSS Vulnerability!
This is one of my interesting writeup for the vulnerability I found on one of Google’s sub domains.
I started to test Google for vulnerabilities in the hope of earning some bounties and to register my name in their Google Bughunter Hall of Fame Security Researchers list!
Writeup:
I Used tools like Knock Subdomain Scan, Sublist3r and other recon tools to find the sub domains of Google.
Using some recon tools, I gathered many subdomains and interestingly I visited https://tez.google.com/ (now Google Pay). I found some parameters on the URL containing referrer id’s passing some values.
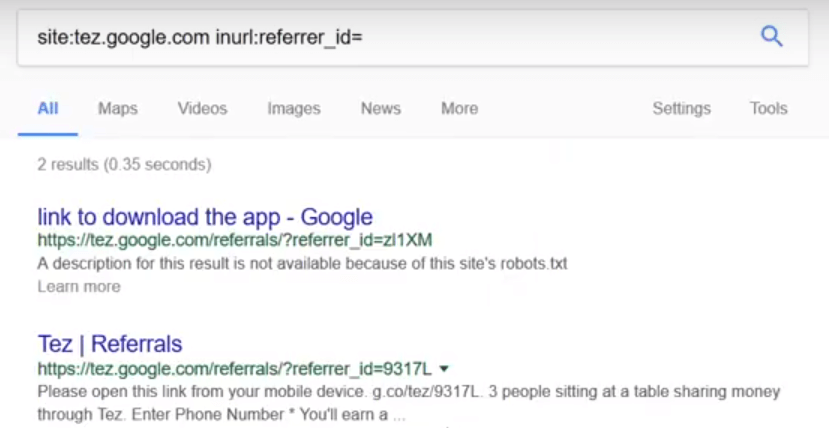
I used the Google Dork to filter out the specific search operators containing in the sub domain.
site:tez.google.com inurl:referrer_id=
I got some of the referrer_id’s in the search result like below.
I tried all the possible ways to exploit the publicly visible referrer_id and my bad luck, I couldn’t find any!
Interestingly, I found the referrer_id’s getting reflected in the part of the web page.
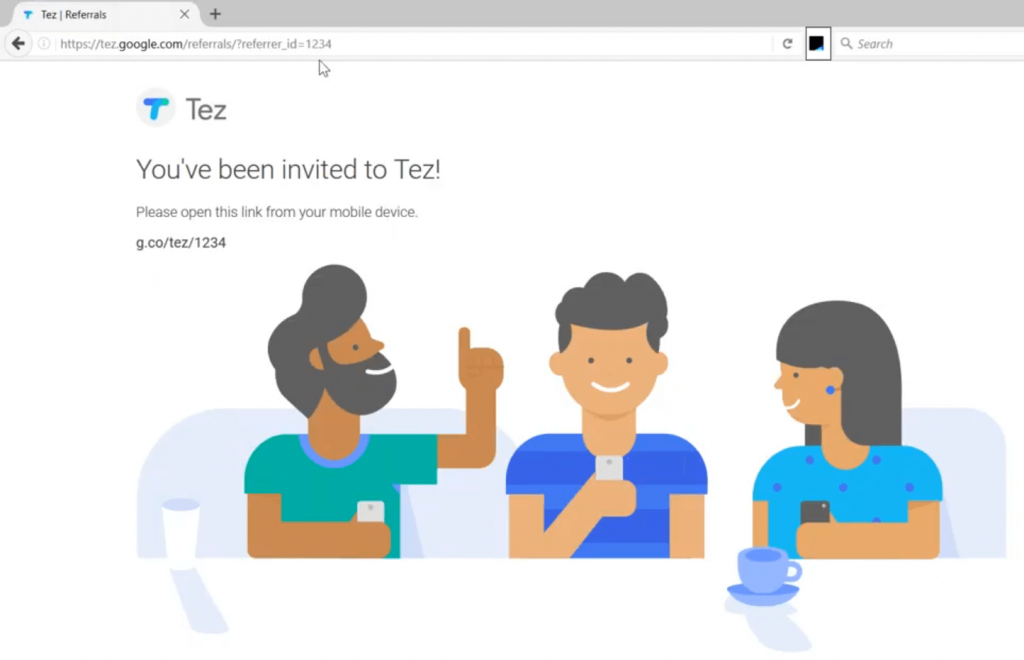
To my luck, I tried popping an XSS and it is XSS!
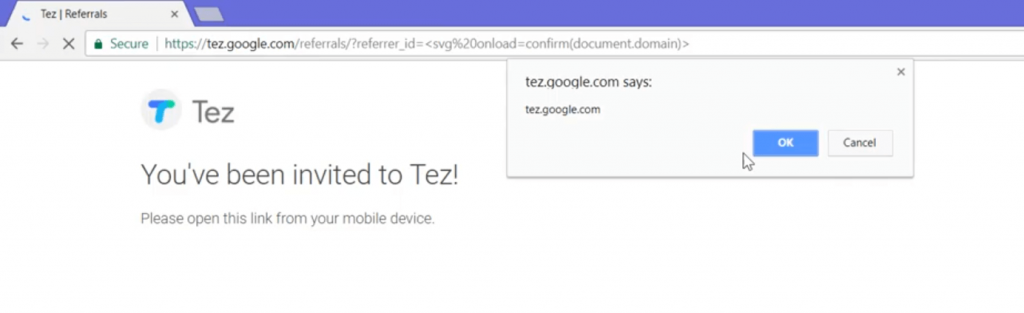
I reported this vulnerability to Google and as per Google Vulnerability Reward Program (VRP).
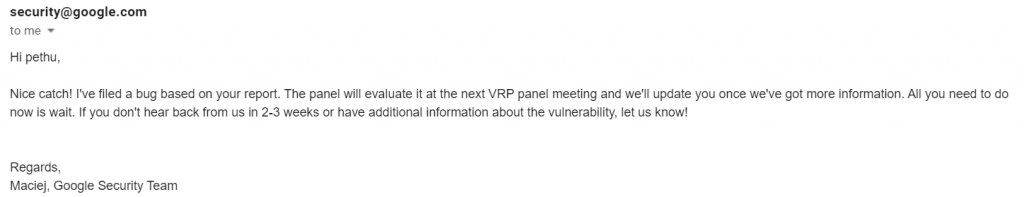
Soon after I report, Google triaged my report and asked me to wait for the bounty amount and Hall of Fame.
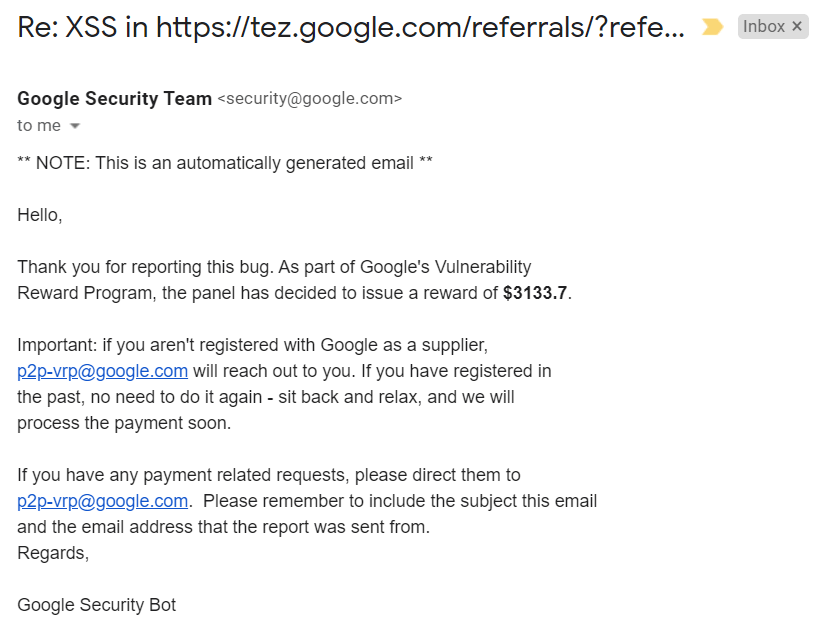
And after waiting for some days, I received a mail from Google Security Team that I’m rewarded with $3133.7 bounty as this is just a DOM based XSS.
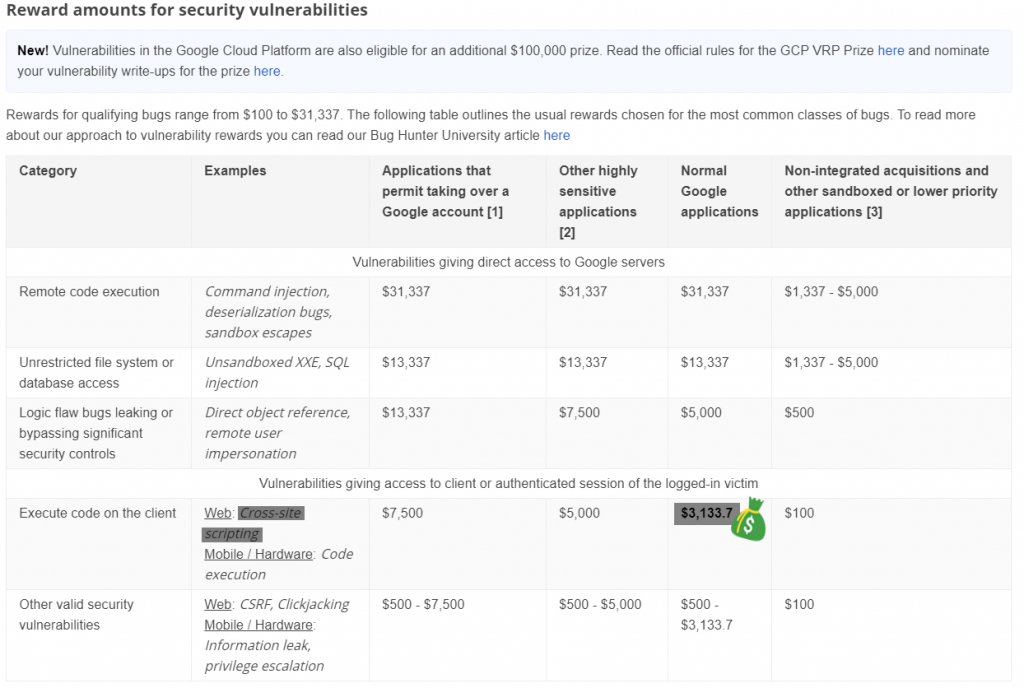
As per Google’s VDP, my vulnerability report falls on the below mentioned category and so $3133.7 bounty.
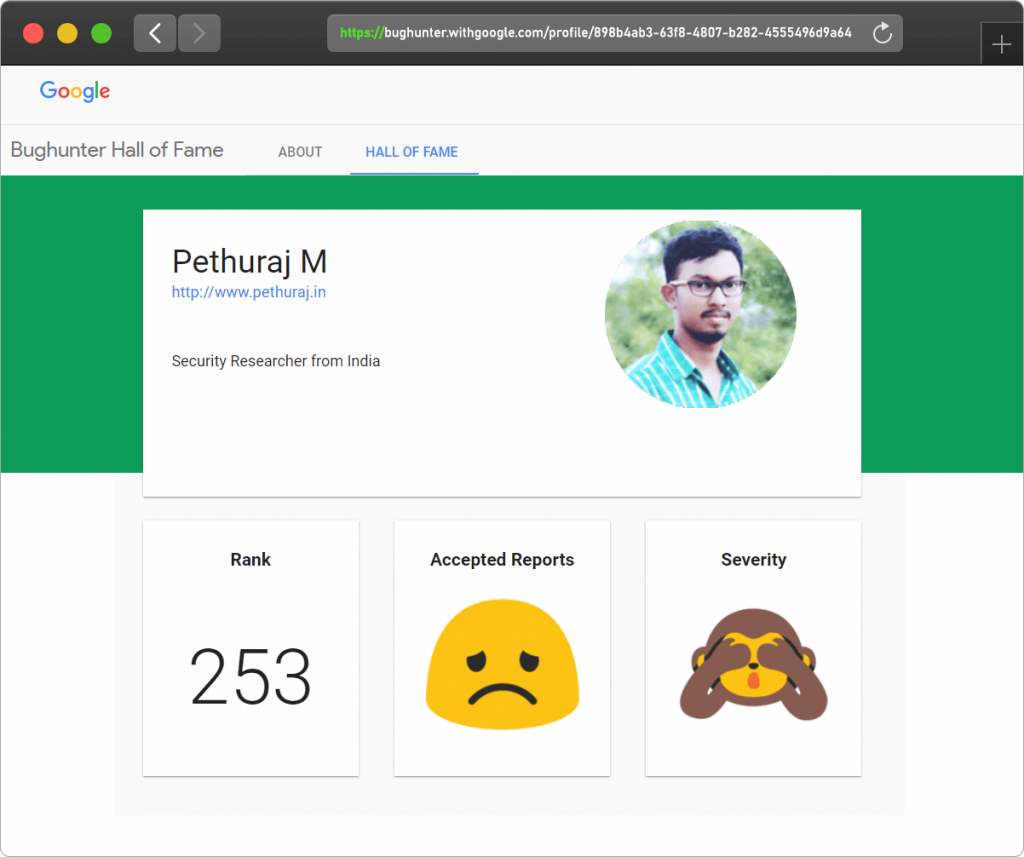
Along with bounty, I’ve also been added to Google Hall of Fame! Ranked 253 among 800 other Security Researchers.
That’s it in this writeup!
To find all my Acknowledgements / Hall of Fames / Bug Bounty journey, Visit https://www.pethuraj.in
Stay tuned for more writeups.
Thank you
You may like

How to use Burp Suite Like a PRO? PART – 2