Microsoft Bug Bounty Writeup – Stored XSS Vulnerability
This blog is about the write up on Microsoft on how I was able to perform Stored XSS Vulnerability on one of the subdomains of Microsoft.
I performed initial recon on the Microsoft domains and gathered some sub domains.
Recon
For recon and especially for subdomain enumeration – I use tools such as Knock, Subrake, Sublist3r, Amass, etc.
Never rely on a single tool for recon as you may miss out your targets.
I gathered all the possible enumerated sub domains and picked some targets to test.
I picked https://storybook.office.com (domain discontinued) for testing and started the recon process for the target.
Interestingly there was a signup and I registered to perform tests for privilege escalation and other issues.
I came across a scenario where the user defined inputs are being stored on the target as this is basically a story publishing platform.
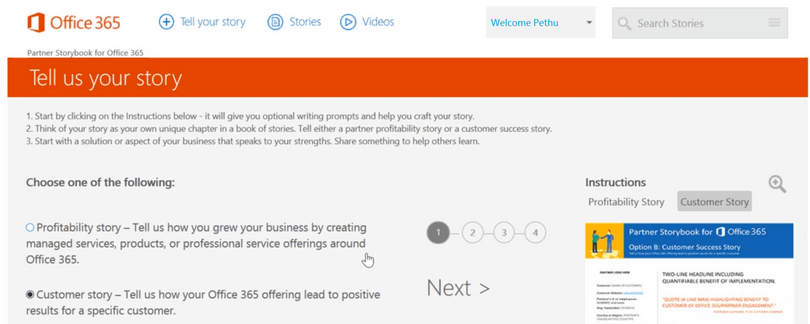
I found an option where users can share their stories. So I tried XSS Vulnerability on those input fields.
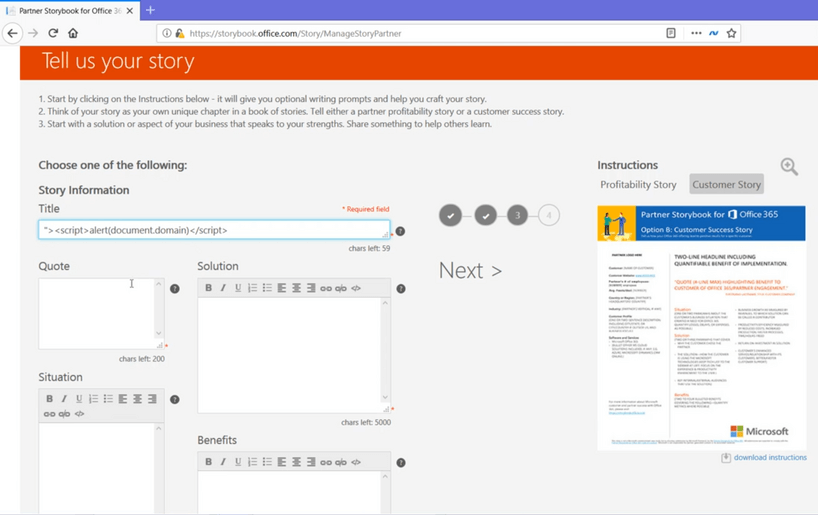
I used a simple XSS payload and added a story.
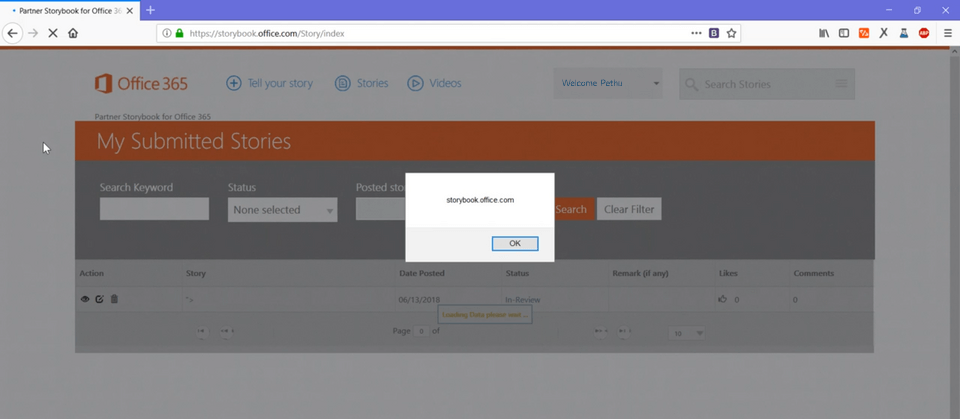
On the next screen is a popup for my XSS payload and it is a Stored XSS Vulnerability on the Microsoft portal.
After reporting this vulnerability to Microsoft I have been acknowledged in their Hall of Fame.
It wasn’t a very hard bug to find, maybe I found the right target at the right time.
Thank you!
You may like

How to use Burp Suite Like a PRO? PART – 2